IT | Security | Emotet comes back to Japan
Emotet has returned after it was taken down
From this month, Emotet activities seem to start threatening Japanese companies again. As you know, Emotet threatened companies all over the world since 2014, especially it was the most active in 2019 but their threat seemed to weaken recently after it was taken down by a lot of effort among cyber security organizations and researchers.

1. What is Emotet?
It says that Emotet was found in 2014 as malware for the banking Trojan. It attempted to sneak on the computers and steal or rock your information in your computers. This malware was gradually distributed via malicious spam email campaigns and became one of the most widely distributed threats over the past several years.

2. How does Emotet compromise your computers?
There are three cases to be compromised by Emotet. First, Emotet distributes an email to you by itself. In the second case, the compromised laptops in your organization spread out malware to other laptops(Lateral Movement). In the third case, another malware, Trickbot, brings Emotet.
And there are four patterns to be compromised by an email. Pattern one is attacking with URL links in Email messages. Users click the URL link in an email and Emotet is downloaded. And pattern two, pattern three and pattern four use attached files with emails. Pattern two hasn’t recently been detected but this is the usual pattern of Emotet, then you should also care about it.
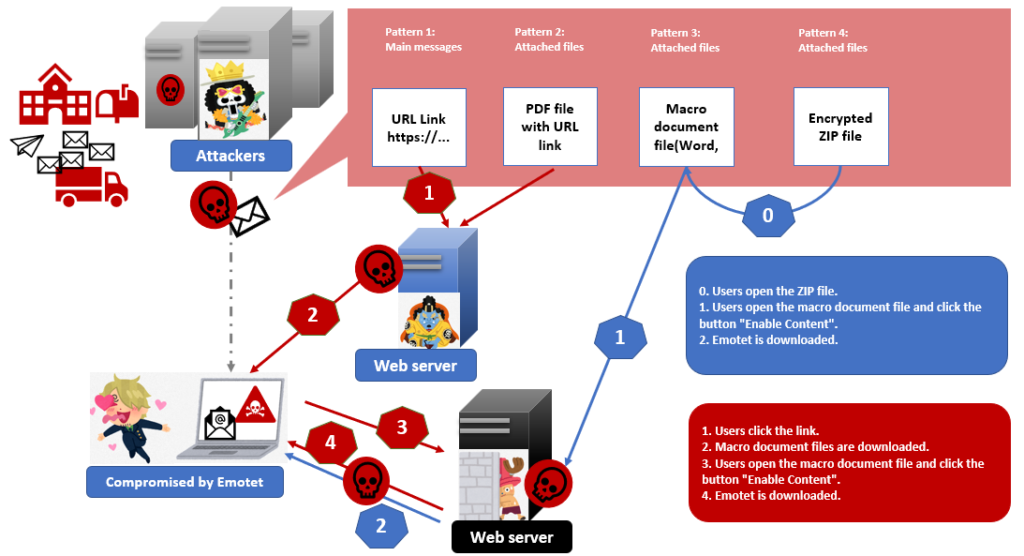
In all patterns, users open the macro files and enable “Enable content”, then this makes macro executed. It’s very difficult for users to find that their information is stolen including emails, attached files, passwords, and so on. What’s worse, they send those Emotet emails to other organizations or users. And also, Emotet can be infected via internal networks, so it could be that all laptops in organizations will be compromised by Emotet after a laptop is attacked.
3. What is different between new Emotet and preveous one?
What is New Emotet different from the previous one? The way of connection and encryption are different. Network traffic for C&C became HTTPS from HTTP, and pattern four above the image is the new pattern actually. Macro documents used to be attempted with an Email, but ZIP files with a password are now available.
4. What can you do for this threat?
What you can do is the same as the measure for the previous one. You should not open the office document files attached to emails, and not click the URL link in emails. Even if you open the file, please stay calm. It will be ok if you don’t click “Enable content” because the macro is not executed.
Related articles:Malware | Japan Teams, IT Learning | Security | Malware | Japan Teams
More detail & Information source: Cisco Talos Intelligence Group – Comprehensive Threat Intelligence: Back from the dead: Emotet re-emerges, begins rebuilding to wrap up 2021, Emotet botnet returns: What CISOs need to know – Tech Monitor, 【注意喚起】マルウェアEmotetが10カ月ぶりに活動再開、日本も攻撃対象に | セキュリティ対策のラック (lac.co.jp), Emotet | What is Emotet Malware & How to protect yourself (malwarebytes.com)
fin
|
|
![[商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。] [商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。]](https://hbb.afl.rakuten.co.jp/hgb/20e00fbc.dcc74e5c.20e00fbd.9b562f6c/?me_id=1278256&item_id=11649585&pc=https%3A%2F%2Fthumbnail.image.rakuten.co.jp%2F%400_mall%2Frakutenkobo-ebooks%2Fcabinet%2F5562%2F2000000215562.jpg%3F_ex%3D240x240&s=240x240&t=picttext)


