Easy! IT | WEB | Digest access authentication
This article is a rough explanation of Digest access authentication.
Everything might be not exactly correct in this article but it’s very useful for beginners to understand IT terms. If you want to learn IT but you don’t have any experience to work in the IT industry, I wish it helps you to understand IT. And I hope this article makes you study IT more.
Let’s start our 3 minutes lesson!
What is Digest access authentication?
- Digest access authentication is one of HTTP authentication.
- Digest access authentication is also called Digest authentication.
- Digest access authentication is used to confirm the identity of a user.
- Digest access authentication is more secure than Basic authentication.
If you don’t know the basic web technology, I suggest you read the following articles before you read this article.
Easy! IT | WEB | World Wide Web | Japan Teams
Easy! IT | WEB | HyperText Transfer Protocol | Japan Teams
Easy! IT | WEB | HTTP Authentication | Japan Teams
Easy! IT | WEB | Basic access authentication | Japan Teams
1. Summary of HTTP Authentication
HTTP Authentication is a method by which the user of a web browser can authenticate itself as a user to the WEB server or a web application in order to be authorized for further access. And there are two methods which are well-known. They are Basic authentication and Digest authentication.
Summary of Basic authentication
Firstly I explain typical HTTP Basic authentication traffic between HTTP clients and HTTP servers.
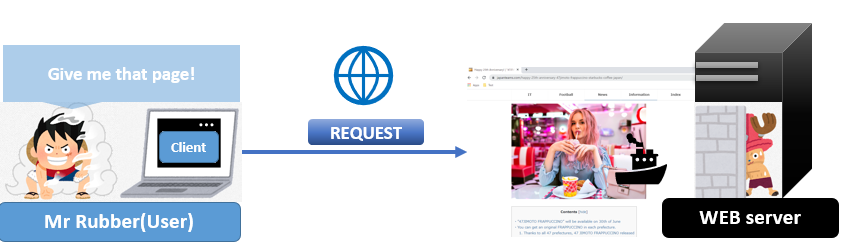
1. Page request from clients(Server side)
A client asks the WEB server to give the page which the user wants to check. He doesn’t request the authentication page because he doesn’t know that he needs to log in at first.
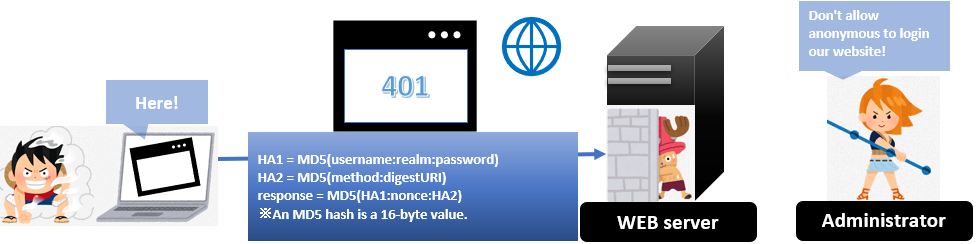
2. The response code 401 (Server side)
The WEB server returns 401 code to tell the client what kind of information servers need.
3. Imput necessary information (Client side)
A client asks the user to input information, such as ID and Password. A user can cancel it at this moment. If a user input his ID and password, a client sends a request with that information added into the authentication header field.
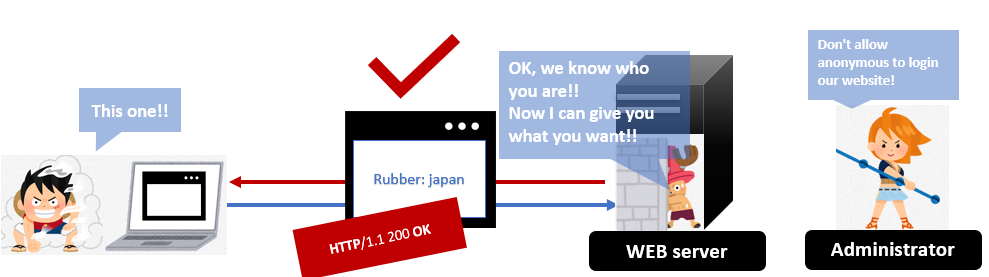
4. Return the results(Server side)
If the authentication is successful, the server accepts the request. But if his ID or password is wrong, the server will return 401 again to reenter the ID and password.
There are security risks
When a client termites data(IDs and Passwords) with Basic authentication, those data are not encrypted. So it’s easy for hackers to do theft or interception them, like a Sniffing attack. Then, Digest authentication improved this weakness. HTTP digest authentication is designed to be more secure than Basic authentication.
2. Flow of Digest authentication
1. Page request from clients(Server side)
The first step is the same as Basic authentication. A client asks the WEB server to give the page which the user wants to check. He doesn’t request the authentication page because he doesn’t know that he needs to log in at first.
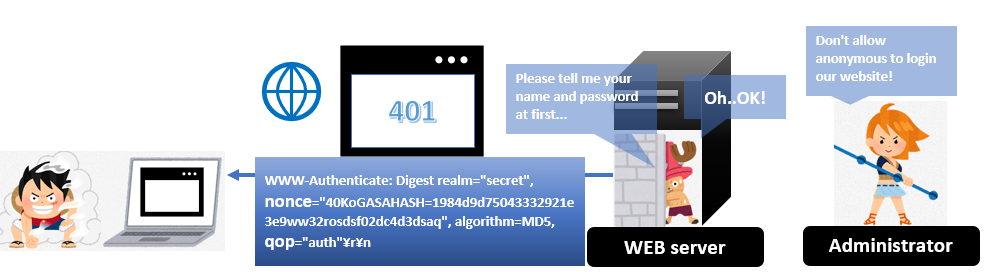
2. The response code 401 with tokens (Server side)
The WEB server returns 401 code to tell the client what kind of information servers need. And this time, the server also sends a server-generated nonce value and “quality of protection” (qop).
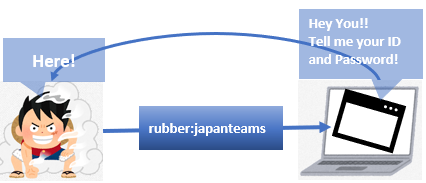
3. Imput necessary information (Client side)
A client asks the user to input information, such as ID and Password. A user can cancel it at this moment. If a user input his ID and password, a client sends a request with that information added into the authentication header field.
4. A client generates random nonce(Client side) and returns to the server
A client increments nonce and creates another nonce based on ID and Password. A Client creates a response with those values. An example of MD5 is here.
Response = MD5( MD5(HA1) “:” nonce “:” nc “:” cnonce “:” qop “:” MD5(HA2) )
The HA1 and HA2 values used in the computation of the response are the hexadecimal representation (in lowercase) of the MD5 hashes respectively.
A client returns information required by the server, such as username, realm, nc(nonce count), nonce, cnonce, qop) and response.

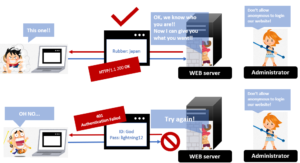
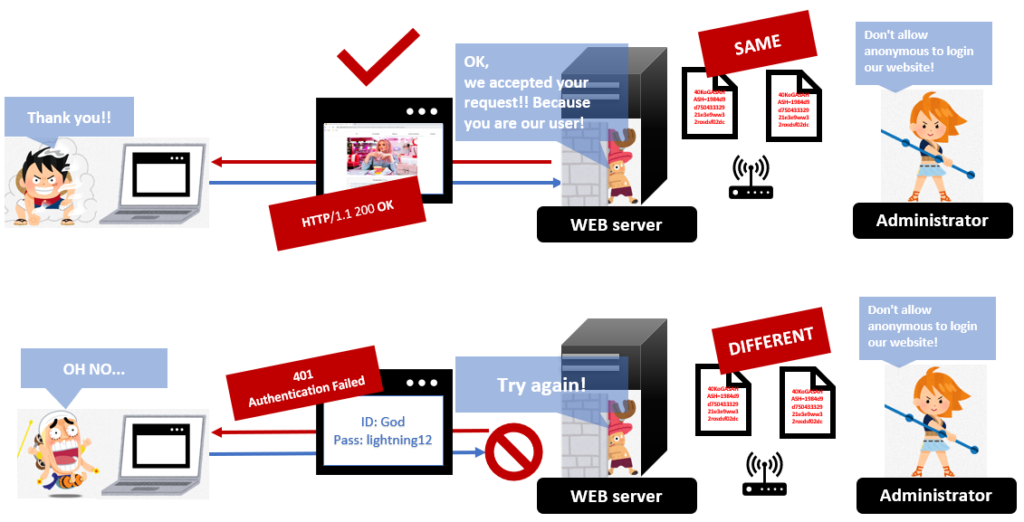
5. The server checks nonce and conce
The WEB server checks if information(nonce, conce, and so on) from the client. The server compares the information with the password stored as a hash in the server. If they are corresponding, the authentication is successful and the server returns the contents. But if they are different, the server returns a 401 response code to ask the client to try again.
3. Security issues
Now it can be to analyze this hash function, and now HTTP data is secured by HTTPS.
This is the rough explanation of Digest access authentication. If you want to know more information. Please check other websites because I’m afraid to say that this website is for beginners!
Information source: Digest access authentication – Wikipedia
fin
|
|
![[商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。] [商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。]](https://hbb.afl.rakuten.co.jp/hgb/20e00fbc.dcc74e5c.20e00fbd.9b562f6c/?me_id=1278256&item_id=19467142&pc=https%3A%2F%2Fthumbnail.image.rakuten.co.jp%2F%400_mall%2Frakutenkobo-ebooks%2Fcabinet%2F3114%2F2000008863114.jpg%3F_ex%3D240x240&s=240x240&t=picttext)