Easy! IT | Security | SQL injection
This article is a rough explanation of SQL injection.
Everything might be not exactly correct in this article but it’s very useful for beginners to understand IT terms. If you want to learn IT but you don’t have any experience to work in the IT industry, I wish it helps you to understand IT. And I hope this article makes you study IT more.
Let’s start our 3 minutes lesson!
What is SQL injection?
- SQL injection is the type of cyberattack.
- SQL injection is used to execute malicious SQL statements.
1. What is SQL?
SQL injection is used to execute malicious SQL statements. When do you use SQL statements? For example, you input a username and a password when you log in to the web application. And you can access the web application if your ID and your password are correct.

You can only see the web interface. But actually, web servers provide the website, and web servers store a lot of information into a database. Usually, database servers provide the database.
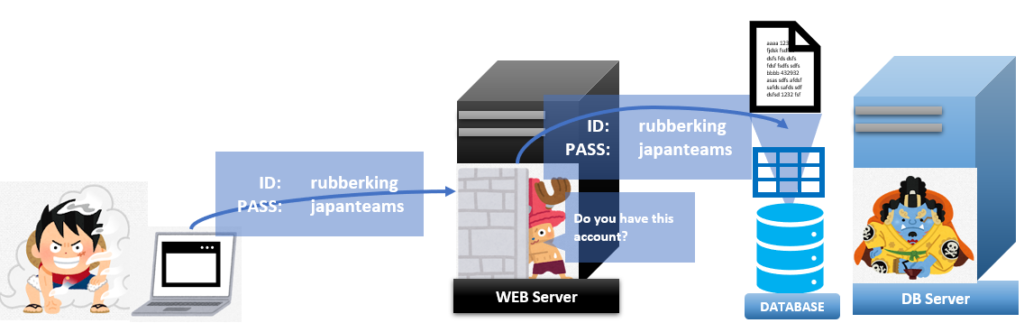
You use the text box when you input your ID and password, but webservers give IDs and passwords with the special statement for the database. One of those statements is provided by SQL(Structured Query Language). The example of the SQL statement of the above image is here:
SELECT id,pass FROM login_user WHERE id=’rubberking’ AND pass=’japanteams’;
2. SQL injection
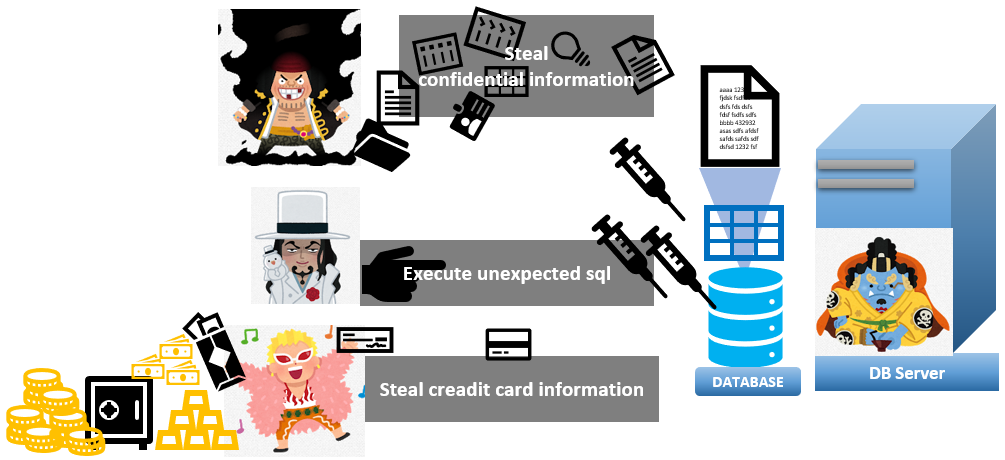
SQL injection is a code injection technique, which is used to execute malicious SQL statements. What can hackers do with SQL injection?
- Extract sensitive information
- Misuse authentication accounts
- Delete data and drop tables and so on

How to attack
I explain how to do SQL injection. For example, how to make unauthorized login available.
I explained how to log in to the web application. You input values(an ID and a password). If your ID is ‘rubberking’ and your password is ‘japanteams’, the SQL statement is like this:
SELECT id,pass FROM login_user WHERE id=’rubberking’ AND pass=’japanteams’;
If you set ‘ OR 1=1– as a value instead of rubberking, the SQL statement is:” OR 1=1–‘
SELECT id,pass FROM login_user WHERE id=” OR 1=1–‘ AND pass=’$password’;
You can log in to the web application without IDs and passwords. Why? In this example code, a single quote(‘) escapes the string as a prepared single quote (‘) is replaced as a double quote (”). And, 1=1 in SQL is always true. What’s more, SQL databases will ignore the text after the ‘—‘ string as this denotes a comment. So, this code means “Return true(=make the user login)”.
That’s the how-to log in to the web application without accounts.
3. Mitigation
An SQL injection is a well-known attack and, you can easily prevent those attacks by simple measures. But it’s still a big threat. If you have opportunities to manage databases, you can take the following measures against SQL injection.
- Object Relational Mappers
- Web Application Firewalls(WAF)
- Detection
- Parameterized statements
- Escaping
- Pattern check
- Database permissions
Information source: SQL injection – Wikipedia
Related articles: IT Learning | Security | Malware | Japan Teams
fin
|
|
![[商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。] [商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。]](https://hbb.afl.rakuten.co.jp/hgb/20e00fbc.dcc74e5c.20e00fbd.9b562f6c/?me_id=1278256&item_id=16373472&pc=https%3A%2F%2Fthumbnail.image.rakuten.co.jp%2F%400_mall%2Frakutenkobo-ebooks%2Fcabinet%2F9011%2F2000000139011.jpg%3F_ex%3D240x240&s=240x240&t=picttext)