Easy! IT | Security | rootkit
I explain the rough image of the rootkit in this article.
Everything might be not exactly correct in this article but it’s very useful for beginners to understand IT terms. If you want to learn IT but you don’t have any experience to work in the IT industry, I wish it helps you to understand IT and you like to study IT more.
Let’s start our 3 minutes lesson!
What is a rootkit?
- A rootkit is a collection of malware.
- Criminals use rootkits.
- Rootkits don’t leave any proofs after criminals.
1. Definition of rootkits
There are many things to do when you conduct cyberattacks, so those things bother attackers. Then attackers made the package of tools for cyberattacks to reduce procedures for attacks. And these tools include actions to delete the proofs which they attack.
Generally, it’s defined as follows:
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the existence of other software. The term rootkit is a compound of “root” (the traditional name of the privileged account on Unix-like operating systems) and the word “kit” (which refers to the software components that implement the tool). The term “rootkit” has negative connotations through its association with malware.
Rootkit – Wikipedia
What is malware? : IT Learning | Security | Malware | Japan Teams
So let’s see a more rough explanation with images.
2. Rootkits are useful tools for cyberattacks
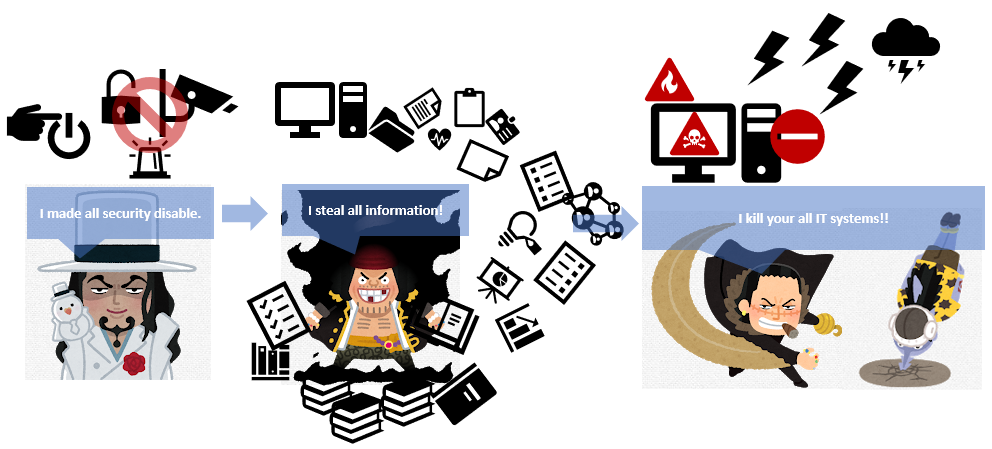
What do rootkits do? They are known as steal your passwords, steal your credit card or online banking information hiding from you. And also they help attackers to disable security software on your computers and track the keys you tap on your keywords to steal your personal information. This ability to disable security software makes attackers invisible. Yes, rootkits make attackers have many ways to attack your IT systems.

Now you can imagine why rootkits are one of the most dangerous attacks, yes? Because it’s very difficult for you to find and delete them.
Here is the list of rootkits.
Type of rootkits
- Hardware rootkit (firmware rootkit)
- Bootloader rootkit
- Memory rootkit
- Application rootkit
- Kernel rootkit
- and so on
Related information: What is a rootkit, and how to stop them | Norton
fin
|
|
![[商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。] [商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。]](https://hbb.afl.rakuten.co.jp/hgb/2104bcd4.f57c18cc.2104bcd5.a8a16c5e/?me_id=1375055&item_id=10804606&pc=https%3A%2F%2Fthumbnail.image.rakuten.co.jp%2F%400_mall%2Fparagon-us%2Fcabinet%2Ffolder_2598%2F234434830.jpg%3F_ex%3D240x240&s=240x240&t=picttext)