Easy! IT | Security | Keylogger
This article is a rough explanation of SQL Keylogger.
Everything might be not exactly correct in this article but it’s very useful for beginners to understand IT terms. If you want to learn IT but you don’t have any experience to work in the IT industry, I wish it helps you to understand IT. And I hope this article makes you study IT more.
Let’s start our 3 minutes lesson!
What is the Keylogger?
- A Keylogger is an abbreviation for Keystroke logging.
- A Keylogger is an action of recording (logging) the keys struck on a keyboard.
- Hacker uses the Keylogger is a type of their cyberattacks.
1. What is a Keylogger for?
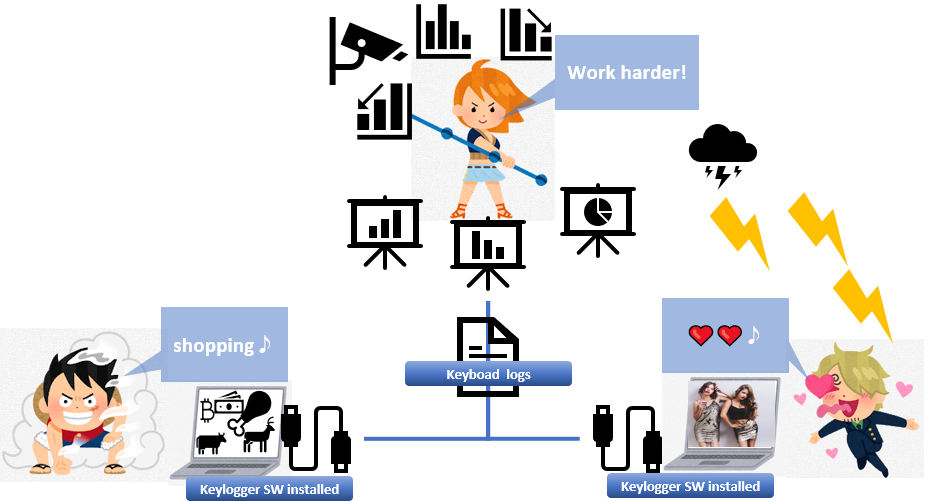
A keylogger is software to record the keys struck on a keyboard. It is very useful for parents to see how their children use their laptops, or it is necessary for the companies to monitor if their employees use the company’s laptops properly.

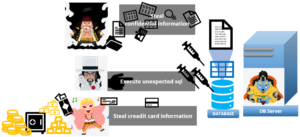
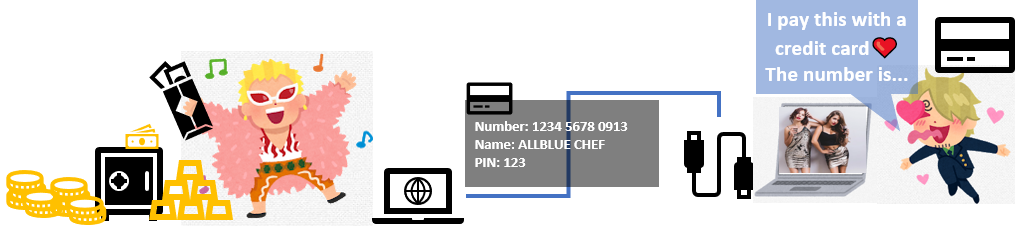
But recording the keys truck means hackers can use this technology to steal information.
2. Type of keyloggers
There are two types of Keylogger. One is software type, and another is hardware type. Software is recently common.
- Keylogging Software
- Hardware Keyloggers
- Mobile Device Keylogging
3. How can you detect a keylogger?
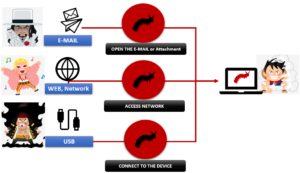
A keylogger makes hackers track and log the keys you strike on your keyboard, capturing any information you typed. But keyloggers are insidious, so you don’t know they’re there, watching and recording everything you type. Because many keyloggers have root-kit functionality. That means they’re hiding in your system.
What is a rootkit?: Easy! IT | Security | rootkit | Japan Teams
If you can prohibit employees to use USB devices, you could prevent hardware keyloggers from working on. But it could be more difficult to find software-based keyloggers. Without security products, you need to monitor the difference, such as your CPU performance, new icons on your laptop, abnormal delays in your activities, pop-up, and so on.
4. How can you protect your information?
1. Alternative keyboard layout

Most of the keylogger software available is based on the traditional QWERTY layout, so hackers can’t understand if you use a different keyboard layout from a common one.
2. Protect your passwords

In addition to using strong and unique passwords, encrypting your passwords and using two-factor authentication can help protect your computers against stealing IDs and passwords.
3. Use security products

Install security products to protect all your devices—PCs, smartphones and tablets. Especially, EDR could help you to detect abnormal activities on your devices.
Information source: What is a Keylogger? | McAfee Blogs, Keystroke logging – Wikipedia, What is a keylogger and how do I help protect myself? | NortonLifeLock
fin
|
|
![[商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。] [商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。]](https://hbb.afl.rakuten.co.jp/hgb/20e00fbc.dcc74e5c.20e00fbd.9b562f6c/?me_id=1278256&item_id=11686051&pc=https%3A%2F%2Fthumbnail.image.rakuten.co.jp%2F%400_mall%2Frakutenkobo-ebooks%2Fcabinet%2F5375%2F2000000255375.jpg%3F_ex%3D240x240&s=240x240&t=picttext)