Easy! IT | Security | DNS cache poisoning
Everything might be not exactly correct in this article but it’s very useful for beginners to understand IT terms. If you want to learn IT but you don’t have any experience to work in the IT industry, I wish it helps you to understand IT and you like to study IT more.
Let’s start our 3 minutes lesson!
What is DNS cache poisoning?
- DNS cache poisoning is one of the Cyberattacks.
- DNS cache poisoning makes Mr caching record the wrong IP address on his cheat sheet.
- DNS cache poisoning aims to make people access attacker’s websites.
If you don’t know DNS well, please check the following articles in advance!
What is DNS? IT Learning | Network | DNS | Japan Teams
What is an Authoritative name server? IT Learning | Server | Authoritative name server | Japan Teams
1. Caching DNS server has a cheat sheet
There are two DNS servers. One is “Authoritative name server”. Another is called Caching DNS Server. Laptops usually ask Mr Caching DNS server the first question. If he can’t answer the question, he will ask Ms Authoritative name server.
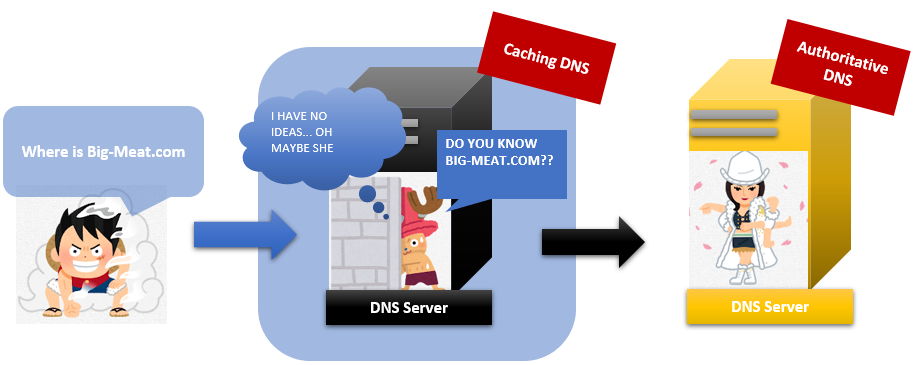
When Ms Authoritative receives the question from Mr Caching, she checks her job handbook called “Zone file”.
What is a Zone file? IT Learning | Server | Zone file | Japan Teams
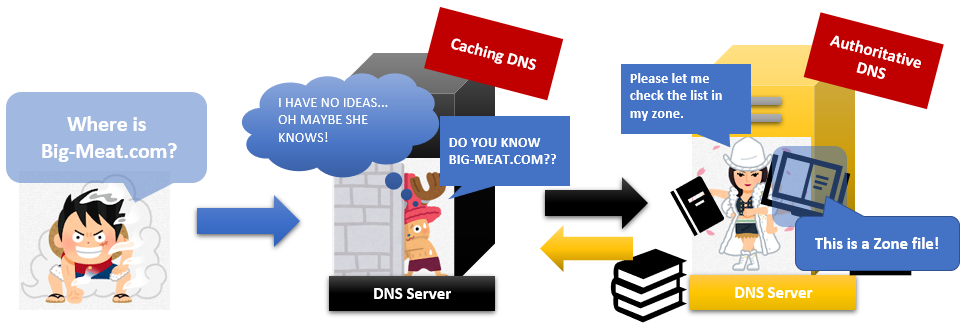
Ms Authoritative checks her zone file when she answers the question from Ms. caching DNS.
If Ms Authoritative doesn’t have the answer, she will tell Mr caching another Authoritative name server. If she knows answers, she will answer the question.
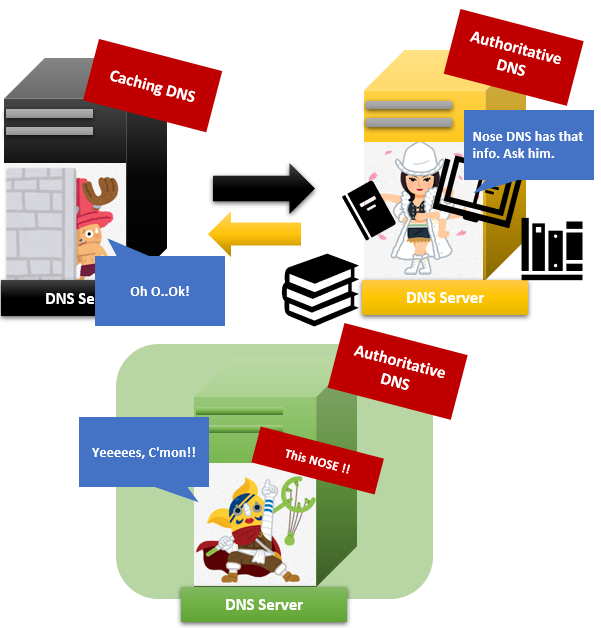
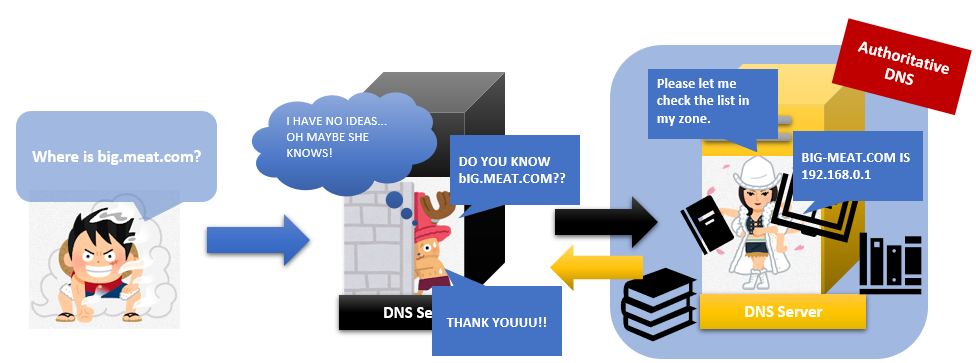
And Mr caching scares Ms Authoritative a little bit. So Mr caching always take note of her answers on his cheat sheet. We call this Mr caching note “Cache”, and taking note “Caching”. Mr caching doesn’t ask Ms Authoritative the question if there are answers in his cheat sheet “Cache”! Authoritative name servers decide how long Mr caching can use this information on “Cache”.
That cheat sheet helps Authoritative servers a lot because they don’t have to work at all if Mr caching answers all with his “Cache”. That’s why this name server is called “Caching DNS server”.
2. DNS cache poisoning
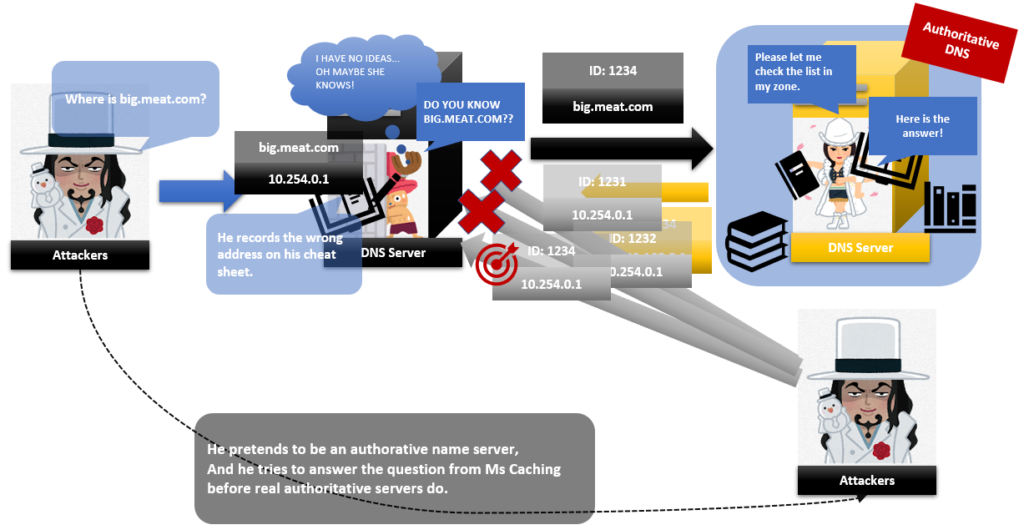
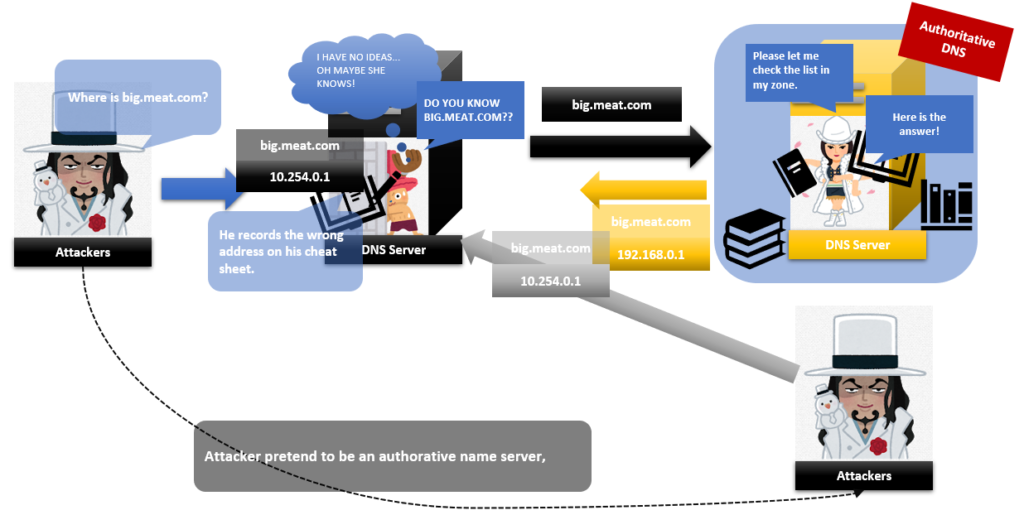
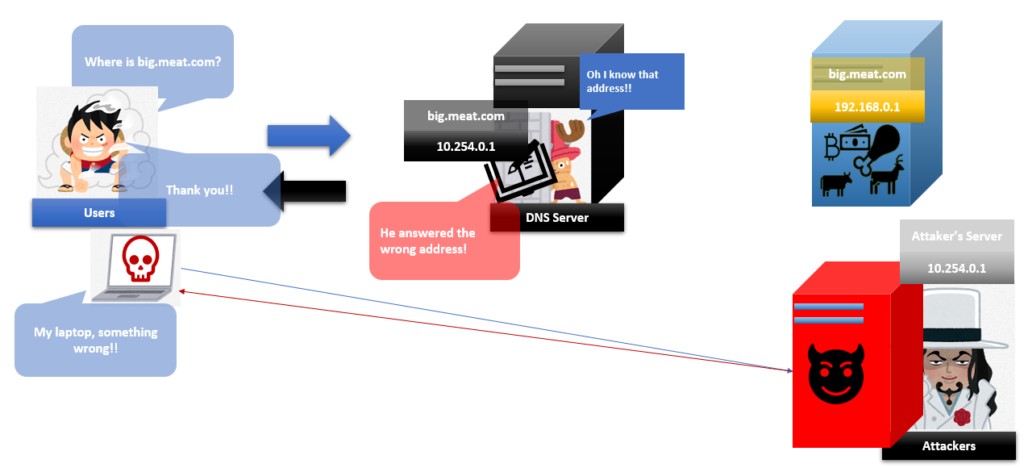
Attackers want that Mr caching DNS server records wrong IP addresses to make people access attacker’s websites. For this,
Cyberattackers use “Caching” feature of Caching DNS servers.
If attackers success to make Mr caching record the wrong IP address on his cheat sheet “Cache”, attackers can make people access their websites which have a lot of traps. Then their attacks will be successful.
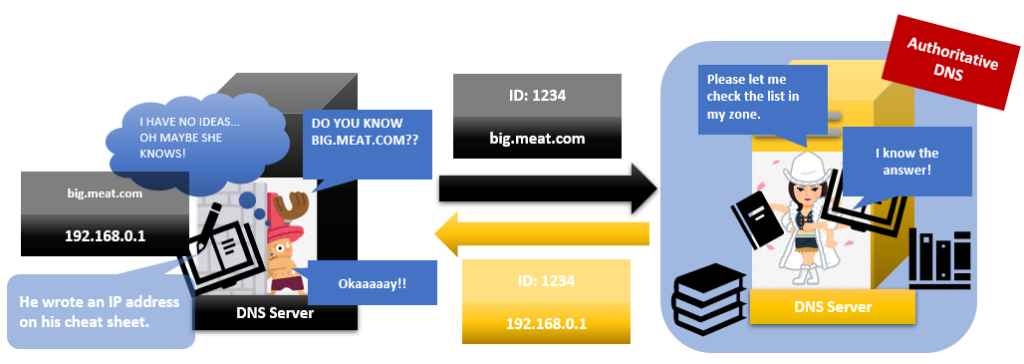
But it was not easy to overwrite it because Mr caching uses ID numbers.
When Mr Caching asks Ms Authoritative the question, he puts an ID number with his question.
And when he receives the answer, he’ll check the ID first. Then if the number is correct, he accepts that the answer is correct. But if that number is incorrect, he rejects that answer as a fake.
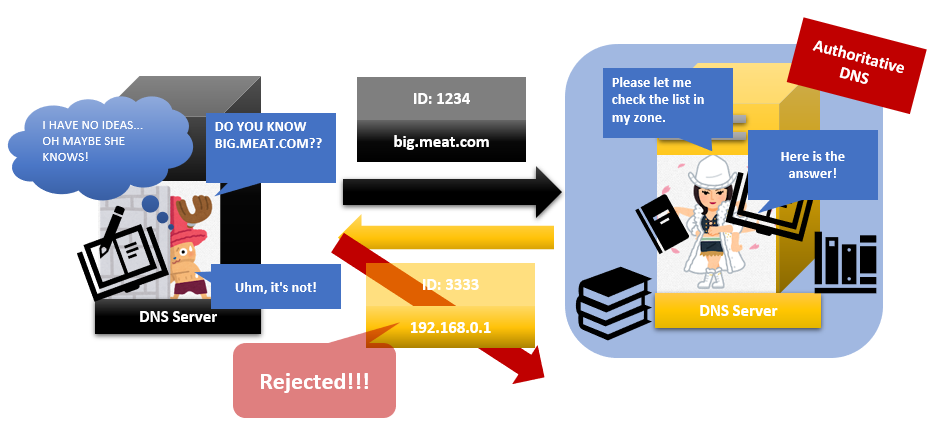
So if attackers want that Mr caching connects the attacker’s server address to their server hostname, attackers pretend to be an authoritative server and answer the question from Mr caching as an authoritative server. But attackers keep sending answers to Mr caching till they find the correct ID otherwise Mr caching doesn’t accept their answers.

3. How to prevent DNS cache poisoning
What can we do to prevent this attack? This attack will be available in case only Mr caching accept the attackers’ fake answer as a correct response, and Mr caching checks IDs if that answer is correct, so attackers try a lot of IDs to find which IDs are correct. It means attackers have no chances if they can’t try a lot of IDs. Or if Mr caching doesn’t ask Ms authoritative, attackers also have no chances to pretend to be an authoritative name server.
- Attakers have a chance to attack when Mr caching asks Ms authoritative to update his cheat sheet.
- Attakers have a chance to attack if the answer from Ms authoritative is late enough to find the correct IDs.
Thus, the following measure is very useful to prevent DNS cache poisoning.
You should set the longer TTLs on your caching DNS servers.
But this measure doesn’t work on a new attack called the Dan Kaminsky DNS vulnerability. I’ll explain it in another article.
Information source is here:
DNS spoofing – Wikipedia, インターネット10分講座:DNSキャッシュポイズニング – JPNIC, DNSキャッシュポイズニング対策:IPA 独立行政法人 情報処理推進機構
fin
|
|
![[商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。] [商品価格に関しましては、リンクが作成された時点と現時点で情報が変更されている場合がございます。]](https://hbb.afl.rakuten.co.jp/hgb/20d1464f.c769ffca.20d14650.9140783f/?me_id=1280779&item_id=10004311&pc=https%3A%2F%2Fthumbnail.image.rakuten.co.jp%2F%400_mall%2Ftenten-store%2Fcabinet%2Fimg00%2Ffiz-opg-lti.jpg%3F_ex%3D240x240&s=240x240&t=picttext)


