Easy! IT | IT Term | Cyber Kill Chain
This article is being edited
This article is a rough explanation of the Cyber Kill Chain.
Everything might not be exactly correct in this article but it’s beneficial for beginners to understand IT terms. If you want to learn IT but don’t have any experience working in the IT industry, I hope it helps you understand IT. And I hope that this article motivates you to study IT more.
What is the Cyber Kill Chain?
- It’s a framework used to understand and combat cyber attacks.
- The Cyber Kill Chain is categorized into 7 steps.
- In general, there are Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command & Control(C2), and Actions on Objectives.
By understanding the Cyber kill chain, you can identify and mitigate potential vulnerabilities in their systems, helping to prevent successful cyberattacks.
1. What is the Cyberattack?
You can skip this chapter if you already know what it is.
In most cases, cyberattacks usually mean attacks via a network including the internet when people talk about them.
Attackers access your IT systems or program from the Internet, and they destroy them or steal confidential information.
However, regardless of whether it is via the Internet or not, it’s defined as malicious activities carried out by individuals or groups with the intent to compromise computer systems, networks, or digital devices, in general.
But, you can think they are usually via the Internet when people talk about the cyber kill chain.
2. The Cyber Kill Chain
It’s said that there are seven steps when attackers exploit systems. And, we refer to that sequence of steps as the Cyber Kill Chain.
1. Reconnaissance
For example, there is a group that tries to get the treasures of the Rubber pirate.

Then, they sent a spy to collect information.
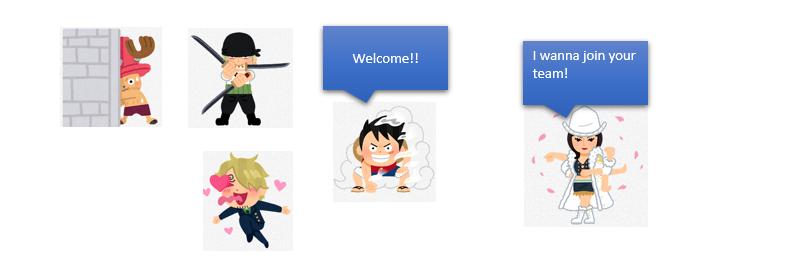
Then, that spy searches for information and she might also have interviews to collect their weak points. This is Reconnaissance.
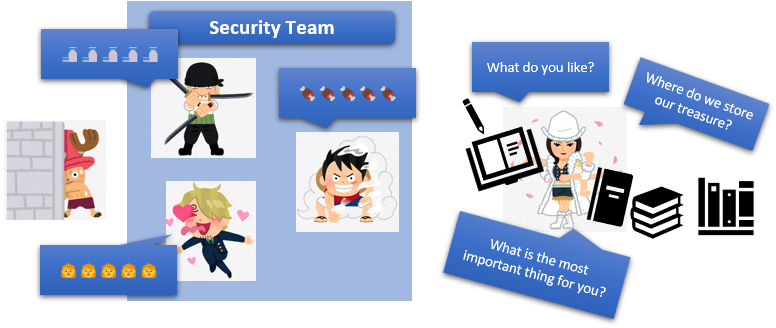
2. Weaponization
She secretly sends information to their analysis.
And, they created weapons based on her information.
3. Delivery
They sent a weapon as a gift and an invitation for the party to stop their security system.
4. Exploitation
A security team joined the party and then their security stopped.
5. Installation
She opened a gift box. Her pals are on the Rubber pirate ship.
6. Command & Control (C2)
She received commands remotely.
7. Actions o Objectives
They steal all treasures.
3. Summary
- Reconnaissance
- The attacker determines what methods to use to complete the phases of the attack.
- Weaponization
- The attacker couples payload code that will enable access with exploit code that will use a vulnerability to execute on the target system.
- Delivery
- The attacker identifies a vector by which to transmit the weaponized code to the target environment.
- Exploitation
- The weaponized code is executed on the target system by this mechanism.
- Installation
- This mechanism enables the weaponized code to run a remote access tool and achieve persistence on the target system.
- Command & Control (C2)
- The weaponized code establishes an outbound channel to a remote server that can be used to control the remote access tool and possibly download additional tools to progress the attack.
- Actions on Objectives
- The attacker typically uses the access he has achieved to covertly collect information from target systems and transfer it to a remote system (data exfiltration) or achieve other goals and motives.
IT Learning | Security | Malware | Japan Teams
Easy! IT | Security | rootkit | Japan Teams
fin